In an interconnected world where information flows seamlessly across networks, protecting sensitive data and preventing unauthorized access have become critical concerns. The increasing frequency and complexity of cyber threats pose significant risks to organizations of all sizes and individuals. As a result, it is imperative to establish robust security measures to safeguard valuable assets and maintain the integrity of networks.
Firewalls and Intrusion Detection and Prevention Systems (IDPS) are two key components that play a pivotal role in ensuring network security. A firewall serves as the first line of defense, acting as a barrier between the internal network and external threats. It examines incoming and outgoing network traffic, applying predefined rules to permit or deny access based on specific criteria. Firewalls help protect against unauthorized intrusions and potential data breaches by effectively controlling access and filtering malicious content.
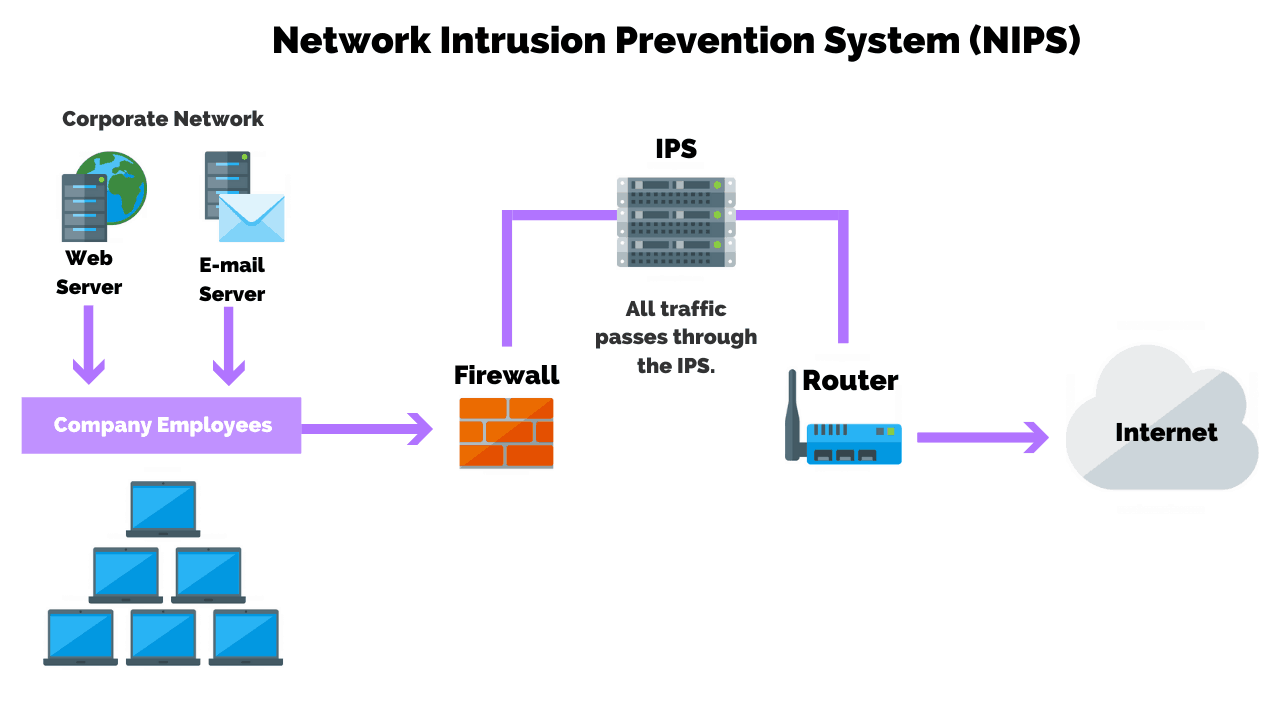
In addition to firewalls, IDPS further strengthens network security by actively detecting and mitigating threats. An Intrusion Detection System (IDS) monitors network traffic for suspicious activities, anomalies, or known attack patterns, issuing alerts when potential hazards are identified. Intrusion Prevention Systems (IPS) take the defense a step further by detecting and taking action to block or neutralize threats in real time, thus preventing potential damage or unauthorized access.
This article will explore the deployment of firewalls and IDPS, their functionalities, deployment considerations, best practices, challenges, and real-world examples.
Firewall: Protecting the Perimeter
A firewall is the first line of defense, protecting the network from unauthorized access and malicious activities. There are various types of firewalls, including packet filtering, stateful inspection, and application-level firewalls. Each class offers unique capabilities and features. Deploying a firewall brings numerous benefits, such as controlling inbound and outbound traffic, preventing unauthorized access, and enforcing security policies. Proper configuration and regular rule-set management are crucial to ensure the effectiveness of firewalls.
Intrusion Detection and Prevention Systems
Detecting and Mitigating Threats An Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) play a vital role in identifying and mitigating potential threats within a network. IDS monitors network traffic and identifies suspicious patterns or activities, while IPS goes further by actively blocking and preventing such actions. IDPS components include sensors, analyzers, and response systems. They employ detection techniques, such as signature-based, anomaly-based, and behavior-based approaches, to effectively identify and respond to threats.
Deployment Considerations
Deploying firewalls and IDPS requires careful consideration of network architecture, topology, scalability, and performance. Understanding the organization’s unique requirements is crucial to determine the placement and zoning of firewalls and IDPS sensors. Integration with existing security infrastructure and ensuring compatibility is essential for seamless operation. Balancing security needs with network performance is a challenge that must be addressed during deployment.
Best Practices for Deployment
Organizations should follow best practices to maximize the effectiveness of firewalls and IDPS. Conducting a thorough risk assessment and threat modeling helps identify potential vulnerabilities and develop appropriate security measures. Implementing a defense-in-depth strategy ensures multiple layers of protection. Regular updates and patch management are necessary to address emerging threats and vulnerabilities. Monitoring network traffic and establishing incident response procedures help detect and respond promptly to security incidents.
Challenges and Limitations
Despite their effectiveness, firewalls and IDPS face challenges and limitations. False positives and negatives in IDPS can lead to unnecessary alerts or missed detections. Sophisticated attackers may find ways to evade detection and bypass firewalls. The deployment of these systems may also impose resource constraints and impact network performance. Furthermore, keeping up with rapidly evolving threats and technologies poses an ongoing challenge for organizations.
Case Studies and Real-World Examples
Examining real-world examples provides valuable insights into the successful deployment of firewalls and IDPS. Success stories highlight the effectiveness of these systems in preventing security breaches. Lessons learned from notable security breaches emphasize the importance of robust security measures. Industry-specific use cases demonstrate the diverse applications of firewalls and IDPS in various sectors.
Deploying firewalls and IDPS is vital to protect networks from a broad spectrum of threats. These systems offer critical defense mechanisms that safeguard sensitive information and thwart unauthorized access attempts. Organizations must comprehend the functionalities, deployment considerations, best practices, and challenges associated with firewalls and IDPS to enhance network security posture. By adopting a vigilant and proactive approach, they can effectively mitigate risks and respond promptly to emerging threats. As technology advances, the future of network security relies on embracing emerging technologies and adjusting security strategies accordingly. Organizations must stay abreast of the evolving threat landscape and leverage innovative solutions to stay one step ahead of malicious actors. By continuously updating and adapting their security measures, organizations can fortify their networks against emerging threats and ensure their valuable data and resources’ confidentiality, integrity, and availability.